 Imagine combining your best and worst week ever into one— welcome to Blippy’s world. This week the site closed a new $11.2 million funding round, got its first picture in the New York Times (leading an article on the new wave of social media sites), and dealt with a true PR nightmare when Google search results revealed the credit card numbers of five users. Although five users represent a teeny tiny fraction of Blippy’s ever-expanding user base, it was the company’s worst fear brought to life. “Five accounts is too many, anything more than zero is unacceptable,” CEO Ashvin Kumar says. “It’s the worst thing that could happen.”
Imagine combining your best and worst week ever into one— welcome to Blippy’s world. This week the site closed a new $11.2 million funding round, got its first picture in the New York Times (leading an article on the new wave of social media sites), and dealt with a true PR nightmare when Google search results revealed the credit card numbers of five users. Although five users represent a teeny tiny fraction of Blippy’s ever-expanding user base, it was the company’s worst fear brought to life. “Five accounts is too many, anything more than zero is unacceptable,” CEO Ashvin Kumar says. “It’s the worst thing that could happen.”
Within the next 24 hours, Blippy is expected to roll out a “go-forward plan” that will likely outline its security policy and assure users that their information is indeed safe with the site. Although Kumar confirms that there has not been a major exodus of users, this could not come soon enough.
Security of course is the one thing that Blippy, a site dependent on users divulging credit card transactions, could not blunder. Maintaining trust is not only critical to scaling up, but to its very survival. So far, the site gets a B- for its handling of the crisis (and I think that may be too generous). To its credit, when the company first heard about the leak on Friday morning, it issued a statement at 10:42 am and immediately reached out to Google. The statement lucidly explained how raw data from credit card transactions was accidently embedded in the HTML source on Blippy’s web pages at some point several months ago (Kumar explained to me that there was an eight-hour window in early February when this bug was active). While a transaction’s raw data string is usually filled with innocuous info about the purchase or the vendor— for a handful of accounts (or more specifically 5) the credit card number was included. Blippy quickly purged the raw data from their HTML codes, but by then, Google had already pulled it into search results.
They win several points here for transparency and swiftly explaining the error, but Blippy should have elaborated on how it missed the leak. Since the vast majority of raw data is benign information, Blippy probably (and understandably) didn’t expect credit card numbers to be visible— but there should have been more nets in place to catch this error or at least an ambitious employee running Google queries to check search results (the search that pulled up the unfortunate data was ” site:blippy.com +’from card’ “, slightly more complex than the typical search but not requiring crazy, jujitsu haxor skills). I expect, or rather hope, Blippy’s upcoming announcement will articulate some of these new preventative measures.
Elsewhere, Blippy wins points for reaching out to affected consumers (the founders personally called the owners of the compromised accounts). But once again, the company loses a few points, for failing to publicly address customer service issues on Friday. In the wake of the NYTimes coverage and the crisis, Blippy’s servers were stressed. For some users, who were looking to close their accounts, that led to error messages and frustration, as evidenced on Twitter:
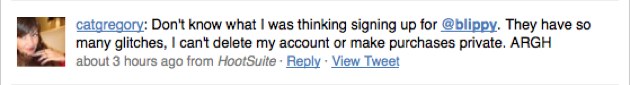
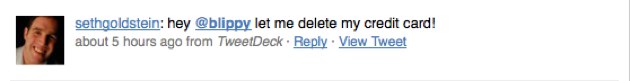
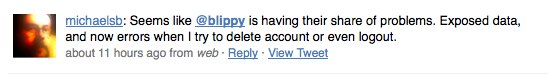
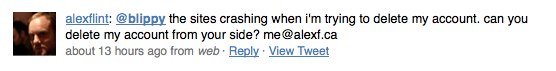
Blippy should have updated its blog or sent an e-mail to users, warning them that they might encounter issues with deleting their accounts this weekend because of server overload. Instead, there was a pool of disenchanted users worried that Blippy was holding their info hostage and fanning fear on Twitter. To Blippy’s defense, Kumar says the team has been working through the weekend to handle complaints and has responded to every user that has reached out to them. It’s just too bad those efforts were not properly communicated. Despite the mistakes, I’m overall impressed with how the founders have navigated their first crisis— Blippy can rebuild and secure the public’s trust. But the founders should know in this game, you don’t get three strikes.